Understand IAM PassRole to Secure your AWS Infrastructure
It’s a very common practice to pass a role to AWS service to allow them to perform tasks on your behalf.
Service can assume the passed role and perform all the tasks permitted by the role. Sounds easy and convenient- Right? 🙂
Now imagine a situation!!!
A normal user(with limited access) creates an Admin role and passes the role to an EC2 instance.
What do you think will happen?
Escalation of Privilege ?? or any error?
Well, that depends upon whether the user has PassRole permission to pass the Admin role to the instance.
Now, what’s IAM PassRole?
Let’s find out…
What is IAM PassRole?
First of all tell me, what do you think about the Action – iam:PassRole in below code snippet?
{
"Version": "2012-10-17",
"Statement": [
{
"Effect":"Allow",
"Action":"iam:PassRole",
"Resource":"arn:aws:iam::123456789012:role/EC2Role"
}
]
}
Well, usually an action in a policy document always maps one-to-one to an API call.
But surprise surprise !!!
iam:PassRole is not an action or API call. You can confirm this by checking IAM API documentation.
That’s confusing enough.
What’s it then?
Basically, IAM PassRole is the permission that controls which users can delegate an IAM role to an AWS resource.
To pass a role (and its permissions) to an AWS service, a user must have iam:PassRole permission assigned to the user’s IAM user, role or group.
Let’s understand this by our analogy- Iam:PassRole example
Bob -> IAM User
EC2Role- Service Role Which can be assumed by an EC2 instance
Bob -> Passes EC2Role to EC2 Service when launching an instance (Pass Role)
Now, the service(EC2) checks if Bob has permission to pass this role to the EC2 instance.
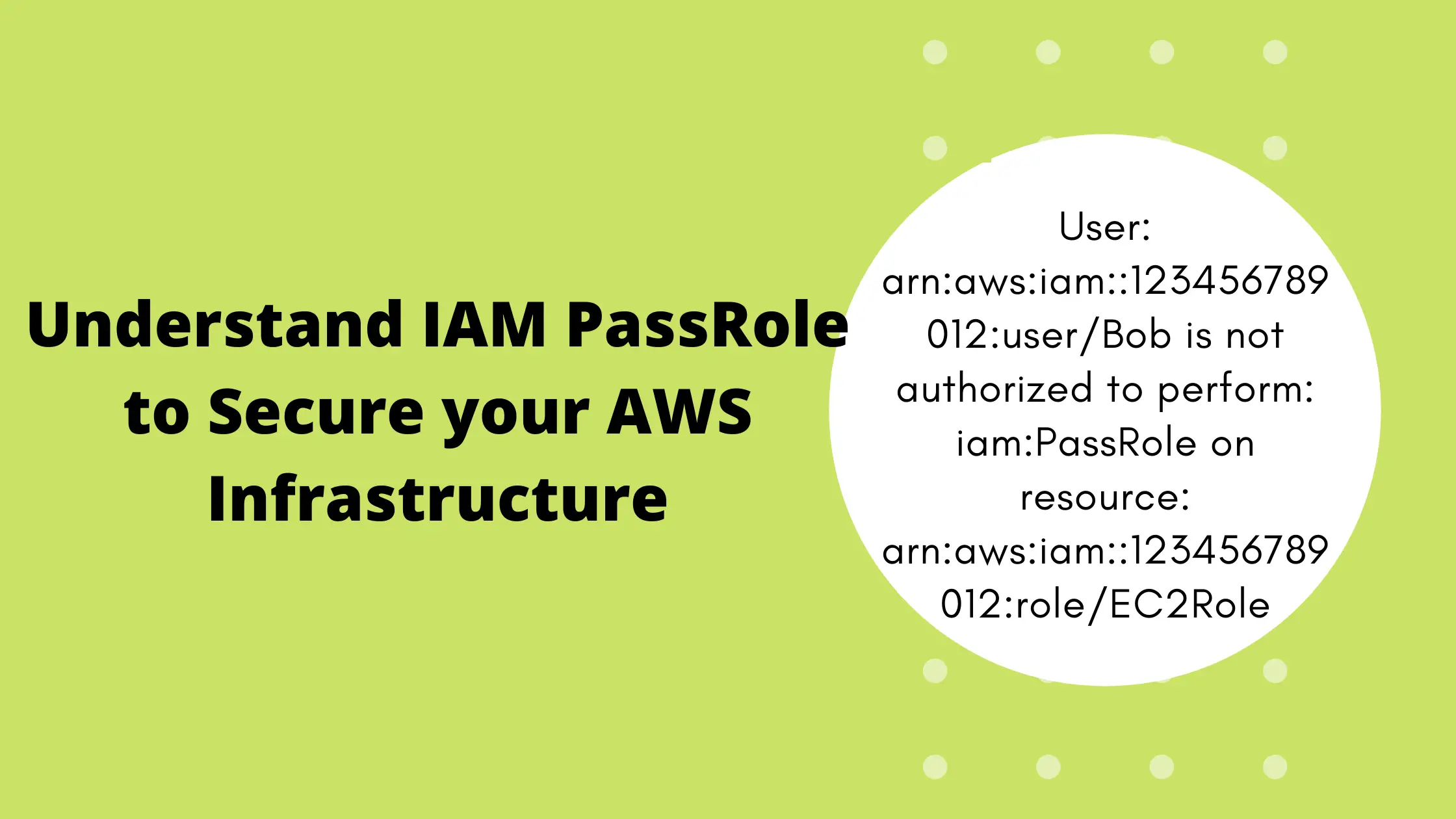
If yes, the instance is launched with that role successfully, If no, an error will be thrown like below.
User: arn:aws:iam::123456789012:user/Bob is not authorized to perform: iam:PassRole on resource: arn:aws:iam::123456789012:role/EC2RoleIn short, Bob must have IAM PassRole Permission for EC2Role to pass the role EC2 service like below.
{
"Version": "2012-10-17",
"Statement": [
{
"Effect":"Allow",
"Action":["ec2:*"],
"Resource":"*"
},
{
"Effect":"Allow",
"Action":"iam:PassRole",
"Resource":"arn:aws:iam::123456789012:role/EC2Role"
}
]
}Why is iam:PassRole Permission important?
The simple answer is Because it’s an additional layer of security to avoid escalation of privilege attacks.
In other words, it helps administrators ensure that only approved users can configure a service with a role that grants permissions.
Let’s come back to the question I asked in the beginning.
Suppose you are a user who has only limited permission. you create an Administrator role and assign it to an EC2.
If there wouldn’t have been the concept of iam:PassRole, you can successfully pass the role to EC2 .
That way you can perform all the admin actions you are otherwise not allowed to do.
But all thanks to PassRole, you can’t do that if you don’t have explicit permission to pass the admin role to EC2.
Making iam:PassRole More Restrictive
In many of the cases, although I see people using iam:PassRole permission. But they tend to give “*” in resource like below.
{
"Version": "2012-10-17",
"Statement": [
{
"Effect":"Allow",
"Action":"iam:PassRole",
"Resource":"*"
}
]
}Why?
Because it’s the easiest thing to do.
What does the above permission mean?
It means that this principle(user) is allowed to pass any role to any AWS Service.
If this user’s credential is compromised, It will allow attackers to create any role they want and assign it to any service to perform any malicious task that they want.
Solution:
Always be specific and follow the principle of least privilege like specifying the specific role that you want the user to pass on.
Conclusion:
To sum up what we learnt in this post-
- To pass a role to an AWS service, a user must have iam:PassRole permission.
- We also learnt why it is important
- Finally, we learnt that using PassRole correctly can help us protect against the escalation of privilege attacks.
Enjoyed the content?
Subscribe to our newsletter below to get awesome AWS learning materials delivered straight to your inbox.
I hope this post was useful to you.
If you liked my post, Please motivate me and help me get better by –
- Adding a comment on this post on what you liked and what can be improved.
- Follow Cloudkatha on –
- Share this post with your friends and colleagues
Please share your feedback and help us get better with time 🙂
Suggested Read:
- Attach an IAM Role to an EC2 instance using CloudFormation
- This is why S3 Bucket Names are unique Globally
- IS S3 region specifc or Global? What do you think?
- AWS S3 Storage Classes: All you need to know
- Create an S3 Bucket Using CloudFormation
- Hello World in AWS Lambda in 5 minutes
- Create DynamoDB Table Using CloudFormation
- AWS Lambda Using Java
- How to Install Docker on Amazon Linux 2 EC2 Instance

2 thoughts on “Understand IAM PassRole to Secure your AWS Infrastructure”
nice explanation