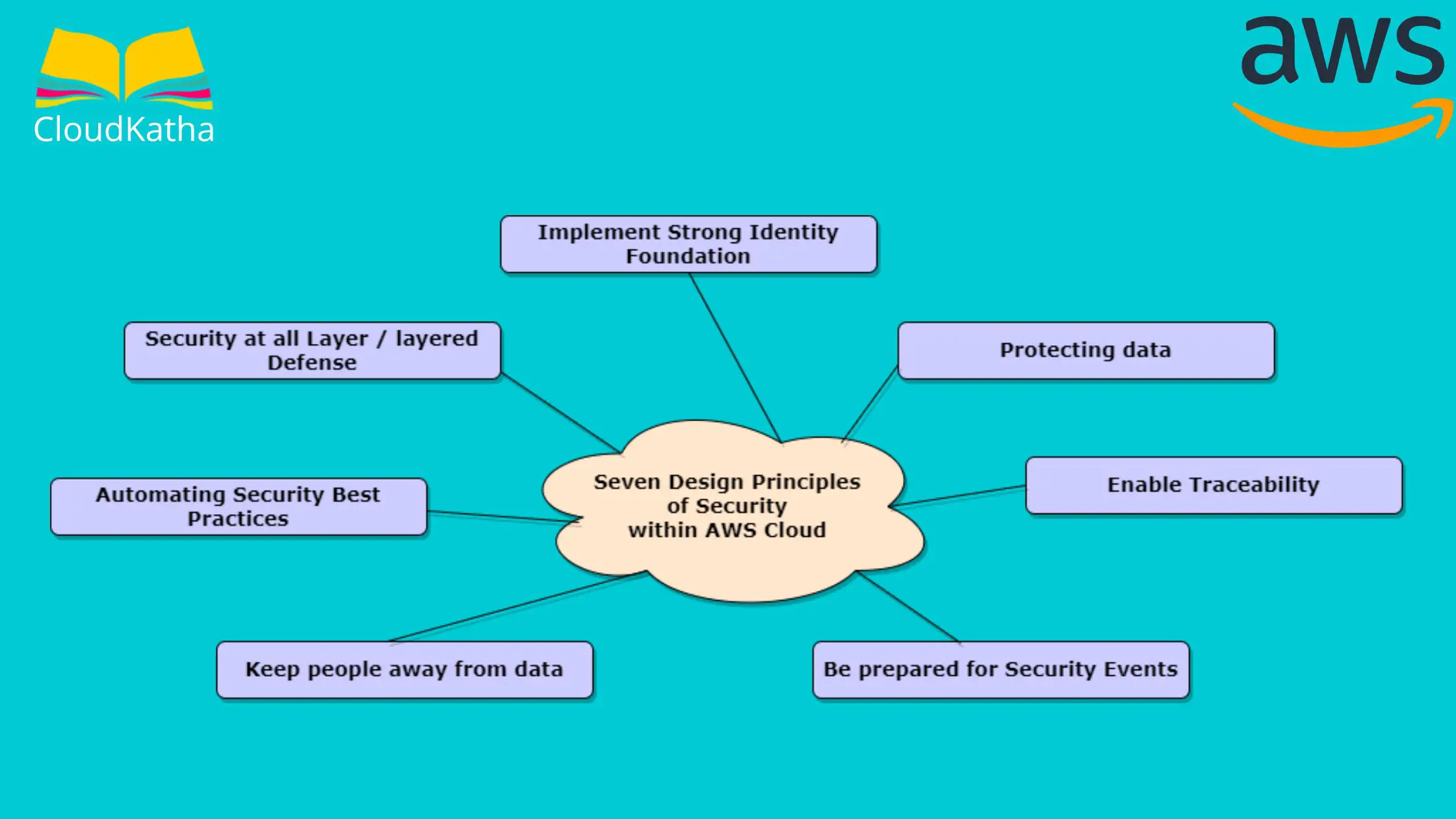
The 7 Design Principles for Cloud Security in AWS Ecosystem
When you are architecting applications on the cloud, The pillars of AWS Well-Architected Framework helps you design reliable, secure, efficient, and cost-effective systems in the AWS cloud.
The security pillar of framework provides an overview of design principles, best practices and resources. Today we are going to discuss about Design Principles for security in AWS cloud to protect or safeguard your AWS environment.
In Amazon Web Services (AWS), security is zero tolerance, i.e., security is the top most priority into AWS environment.
Overview
We’ll be covering what are these design principles of security in AWS? How is this beneficial to enhance the overall security of your workload on AWS?
I hope this article will clarify most of the common questions you might have on design principles for the security in AWS cloud.
Excited to know in details..?? Let’s get started then…!
Don’t want to miss any posts from us? join us on our Facebook group, and follow us on Facebook, Twitter, LinkedIn, and Instagram. You can also subscribe to our newsletter below to not miss any updates from us.
Before We Begin
You must have heard about ‘Shared Responsibility Model‘. In the shared responsibility model cloud provider i.e. AWS is responsible for the ‘Security of the Cloud’, whereas customer is responsible for the ‘Security in the cloud’.
Although customers are responsible for security in the cloud, AWS provides best practices, design principals, tools and resources that you can configure for your system to be secured.
The 7 Design Principles for Cloud Security in AWS Ecosystem
There are 7 design principals for security in the cloud.

Let’s discuss the seven design principles from AWS cloud security prospects –
1. Implement strong Identity Foundation – to manage effectively Identity & Access Management
It is very important to implement strong Identity foundation. It will enable you to safeguard your cloud account and all the associated services, and applications mapped within your AWS ecosystem.
Things you can do for strong identity foundation-
- Enforce Least privilege principle
- Follow IAM best practices
- Role segregation or separation of duties
- Avoid using long term static credentials etc.
2. Enable Traceability – to track what’s going on
Ability to trace, help you understand what’s going on specially during any incident investigations or changes into the environment in real time.
You can enable traceability by-
- Real-time monitoring of Alerts/threats or changes to the environment
- Integrating logs with systems for automatic actions or remediation’s
- Incident investigations or Audit actions etc.
3. Security at all layers – Defense in depth concept with multiple controls
Layered defense means security at all the layers with multiple controls. As a result, you are protected even if one control is being bypassed or failed for some reason. This is also known as Defense-in-Depth concept.
You can implement security at all the layers like-
- Edge network, VPC, Load balancing,
- Instance or Compute services, Operating System,
- Application or Code level etc.
4. Automating Security best practices – To eliminate human errors
As you know there is limitation with human brain. Human error is very likely to happen. It is recommended to automate certain best practices to eliminate the chances of human error.
Here are few security best practices-
- Software based mechanism to scale securely and more rapidly for cost effective solution
- Automated security alerts can be setup to notify the correct team for remediation action
- Automated scripts/set of instructions can execute at certain frequency to identify the problems for necessary actions etc.
5. Protecting data – At rest as well as in Transit
To protect data, It is very important to first classify it properly as per your organizational security policy. Based on the sensitivity, you can have more clarity on what level of security control to deploy for protecting your data throughout the lifecycle.
Considerations for protecting your data-
- Classifying Data as per your organization’s security policy/business need.
- Use mechanism for data encryption both at rest and in transit, tokenization, access control etc.
- You can control encryption in-transit with TLS across AWS services.
Related: AWS S3 Encryption: All You Need to Know
6. Keep people away from data – To reduce direct or manual processing of data
Apart from Least Privilege principle, avoid direct access or manual processing of data, especially when handling sensitive data. It will reduce the risk of human error, mishandling, intentional or un-intentional modification of data.
Few controls to keep people away from data-
- Use Tools or mechanism to lower the requirement for Human access of data
- Avoid direct access or manual processing of data to reduce the risk.
- And of course, apply Least privileges concept to only allow authorized people to access and modify it considering your regulatory requirements if applicable.
7. Be prepared for security events – Effective Incident Handling mechanism
Develop proper incident management and investigation policies & procedure to manage effectively during cyber security events. Follow organizational best practices and train your team members to increase awareness.
Preparations for handing security incidents-
- Develop incident management along with investigation policy & procedure.
- Be prepared for handling security incidents & align with your organizational goal/business need to manage it more effectively.
- Train the team members with necessary policy and procedures for better awareness.
Before we conclude:
So, we have covered here 7 design principles for cloud security in AWS ecosystem. By adhering to these design principles, you can protect your cloud data, system or applications in AWS environment.
Just to remind here, whatever controls you deploy doesn’t give you assurance that breaches will not happen, or your environment will not be compromised. You need to ensure that you are following security best practices and putting necessary approach to minimize the risk to the acceptable level.
Conclusion –
Well, it’s time to summarize today’s learning. In this post we have seen, how the security pillar of AWS Well-architected Framework with helps you protect your data, system, computer network etc. within your AWS ecosystem.
These 7 design principles security pillar discussed above will certainly help the customers to follow the security best practices to strengthen the overall security posture of your workload. Also, It enables you to focus on security since the beginning of the designing the environment within AWS also known as security by design principle.
Wrapping up today’s article here, will soon come-up with another interesting topic, that you may find relevant in terms of AWS Security or cloud security.
Enjoyed the content?
Subscribe to our newsletter below to get awesome AWS learning materials delivered straight to your inbox.
If you liked reading my post, you can motivate me by-
- Adding a comment below on what you liked and what can be improved.
- Follow us on Facebook, Twitter, LinkedIn, and Instagram
- Share this post with your friends and colleagues.