How to Access AWS S3 Bucket from EC2 Instance In a Secured Way
AWS S3 or Simple Storage Service is undoubtedly one of the most used AWS service. If you are using AWS cloud, there are high chances of you using S3 directly and indirectly.
For example – You have deployed your web application on AWS S3. Your application needs to access an s3 bucket to be able to store the user’s photos and to display in their profile.
Very good …
But, do you know that, by default an EC2 instance can not access S3 or any other AWS service.
This is what happens if you try to do so –

Unable to locate credentials. You can configure credentials by running “aws configure”.
The above error is pretty much self explanatory and you know that credential configuration needs to be done.
However, what’s the right way to do that?
Let’s understand that in next section.
Secure Way to Configure Credential on EC2 Instance
To be honest, as soon as we see, credentials not configured error, the very first thing that comes to our mind is using access key/secret key to configure it.
However, configuring credential this way is gonna store your credential on your EC2 machine. Do you think it’s safe?
Of course it’s not. You don’t want any malicious user to get hold of your keys and misuse your account.
What to do then?
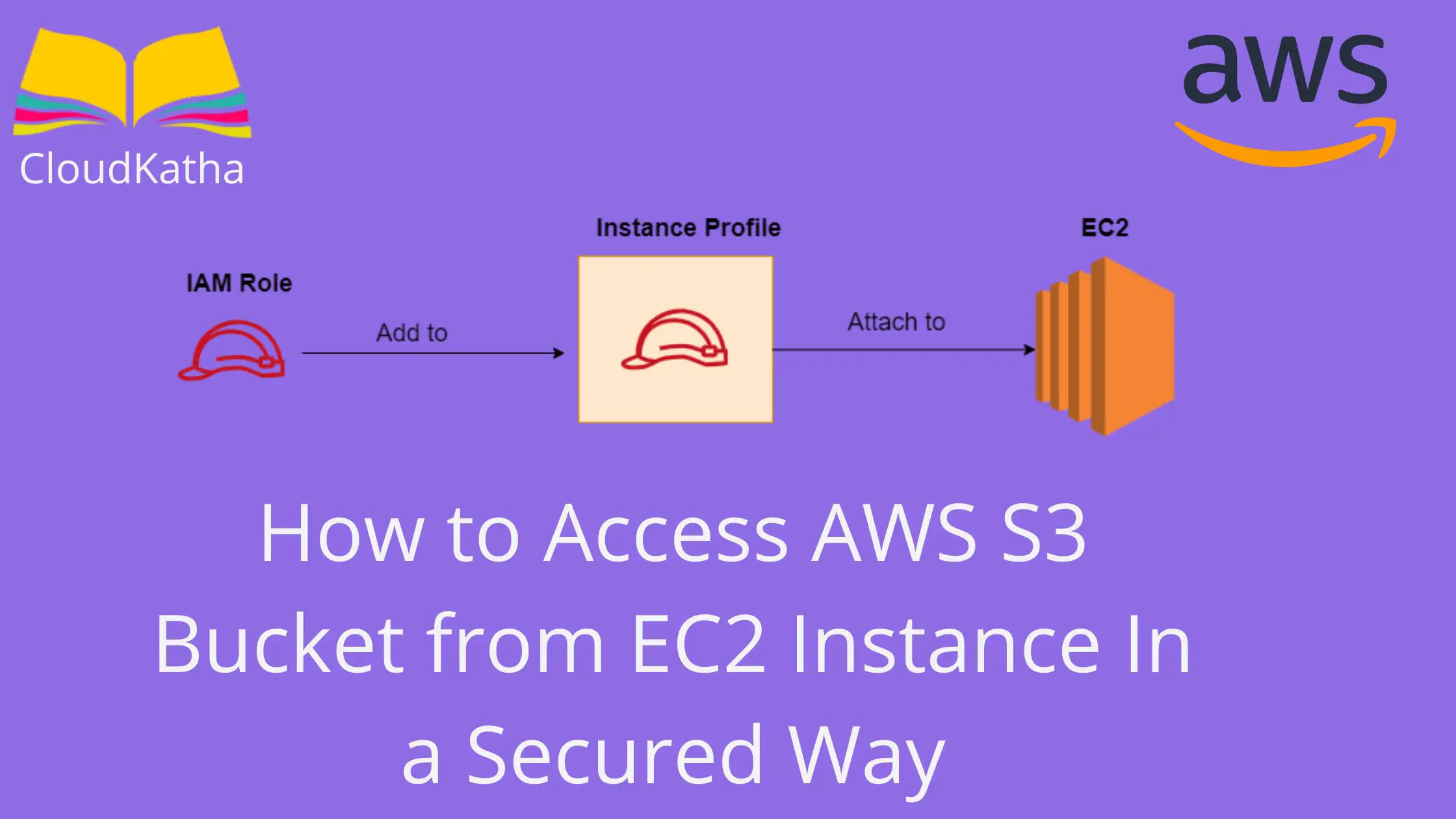
Hmm, you should rather use an IAM role to give permission to your instance. For that, you are required to create an instance profile that will contain your IAM role. After that, attach that instance profile to your instance and tada- everything works fine.
What is EC2 Instance Profile? How to Create one and attach to EC2?
Instance profile is nothing but the container for an IAM role.
- You can use instance profile to pass an IAM role to an EC2 instance.
- An instance profile can only contain one IAM role. However, please note that a role can belong to multiple instance profile.
when you create an IAM Role for EC2 using the IAM Console, it creates both an EC2 instance profile as well as an IAM role with same name.
So, when using AWS console, all we need to do is create an IAM role for EC2 and your IAM profile will be ready to choose or use.
However, this is not the case with CLI or SDK or CloudFormation. Wanna know more- Read here
So, shall we start?
Alright.
Steps to Enable S3 Bucket Access from EC2 Instance
- Create an IAM Instance Profile
- Attach EC2 Instance Profile to Your Instance
- Connect to EC2 Instance using SSH
- Validate Access to S3
Step 1: Create an IAM Instance Profile
Login to AWS Management Console and search for IAM service.
Click on Roles and then click Create role as shown below.
IAM -> Roles -> Create role

Select Trusted entity type as AWS Service and choose EC2 service as shown below-

Click Next
Now you have to add permissions to this role. You can either create a custom policy with your required permission or you can attach an AWS managed policy.
For this tutorial I just need S3 read access, therefore, I am using a managed policy named “AmazonS3ReadOnlyAccess” policy. As you can see I just searched s3 read and this policy came up.

Select the policy and click Next
In the next screen, enter a meaningful role name-

Scroll down , you can also add tags if you need.
Click Create role

In a matter of second, the role is created and you see success message like-

Step 2: Attach EC2 Instance Profile to Your Instance
As we talked earlier that, when we created role, an instance profile with same name was also created. let’s go ahead and attach the created instance profile to our instance.
Select your EC2 instance, click on Actions -> Security -> Modify IAM role

Once you click on Modify IAM role, you are navigated to a screen to choose an IAM role.

I’ll choose the role we created and click on Update IAM role
Role is successfully attached to our Ec2 instance.

Note: Please note that we have created an IAM role for our EC2 instance first and then we are attaching it. However, you can directly start with Modify IAM role and create new IAM role and use that.
Step 3: Connect to EC2 Instance using SSH
We’ll be validating S3 access from instance. And, for that, we need to be connected to EC2 instance.
You can use an SSH client if you wish, I am connecting to my instance using EC2 instance connect (browser option).
Select your instance and click on connect button as shown below-
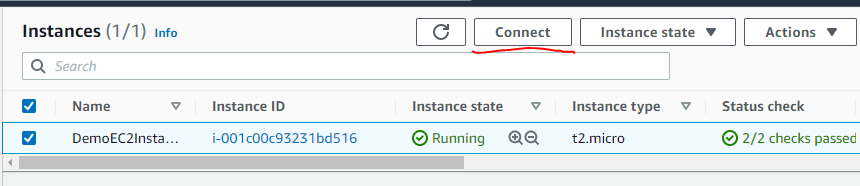
Choose EC2 Instance Connect option

Validate user name and click connect(Different AMI can have different user name for example for linux2 that I choose, user name is ec2-user).
And here we are connected to our instance.

Awesome, lets go ahead with the next step to valid access to s3
Step 4: Validate Access to S3
Type a very simple s3 command-
aws s3 lsIf all is well then this command will return us the list of s3 buckets in our account.

Hey, As you can see, we are able to see list of buckets which meant we can access s3 from our instance.
Also, please note that we have given only read access to our EC2 instance role, so if you try to fire any write command like-
aws s3 mb s3://bucket-nameIt should error out !!!

And yes, it did error out as expected.
Which is so obvious. Because, we have not provided these permission to EC2 role. In this way, using least privilege principal, you can securely provide only required access to your instance.
Conclusion:
In this post, we learnt “How to Access AWS S3 Bucket from EC2 Instance In a Secured Way“
- We can configure credentials using access key/secret key or use role
- Using access key/secret key is unsafe because credentials get stored in the instance
- Using instance role is safer and recommended
- EC2 instance role is used through instance profile however it’s abstracted in UI
In CLI , SDK , CloudFormtaion you actually need to create role, put role in instance profile and then attach the profile to EC2 instance. - We created an IAM role with s3 read only access and attached it
- We validated access to S3
That’s all for today. I hope you found this post helpful. Feel free to drop your questions in comment section.
Enjoyed the content?
Subscribe to our newsletter below to get awesome AWS learning materials delivered straight to your inbox.
Don’t forget to motivate me by-
- Adding a comment below on what you liked and what can be improved.
- Follow us on
- Subscribe to our newsletter to get notified each time we post new content
- Share this post with your friends
Suggested Read:
- How to Attach an IAM Role to an EC2 Instance using CloudFormation
- Difference Between IAM User and Root User
- Create S3 Bucket Policy using CloudFormation
- How to Configure S3 Lifecycle Policy using CoudFormation
- Launch EC2 Instance in an Existing VPC using CloudFormation
- S3 CORS Policy Configuration using CloudFormation

2 thoughts on “How to Access AWS S3 Bucket from EC2 Instance In a Secured Way”
I am beginner in cloud environment, and this article, already solved many queries.
Thank you 🙂