AWS S3 Encryption: Way to Protect Your Data in S3
Have you ever stored some sensitive data in AWS S3?
Ever worried about an S3 server getting in the hold of a malicious user? Will they be able to get hold of your data?
Or Is there a way to protect your data while storing in AWS S3?
Well, S3 gives you an option to encrypt your data. This means, that even If they hold your data, they won’t be able to read /understand it.
Now that’s lovely !!!
That’s the beauty of encryption my friend 🙂
In this post, we will talk about various options that S3 provides to encrypt your data to keep it secure at your own convenience.
Let’s start with understanding a bit of encryption.
Don’t want to miss any posts from us? join us on our Facebook group, and follow us on Facebook, Twitter, LinkedIn, and Instagram. You can also subscribe to our newsletter below to not miss any updates from us.
Related: How to Create an S3 Bucket in AWS Step by Step
What is Encryption?
Encryption is the process of converting your plain-text data/information into an encoded format known as ciphertext.
Encryption usually uses a key to encode your data into ciphertext. Ideally only the authorized person who has the decryption key can only access the original information.
The encryption key is stored separately from the data to ensure the data is protected. Encrypting your data protects it against various kinds of cyber attacks such as data theft, ransomware attack etc.
Suggested Read: 10 Most Comon Types of Cyber Attacks and How to Mitigate Them
Therefore, If you are storing sensitive data in AWS S3, You should always encrypt your data.
Protect Your Data End to End:
To be honest, your valuable data/information at any specific time is either travelling over a network or is stored on a disk.
This means you must encrypt them when they are travelling and while they are stored on a disk.
Let’s get into the details and understand how S3 helps us in protecting our data end to end.
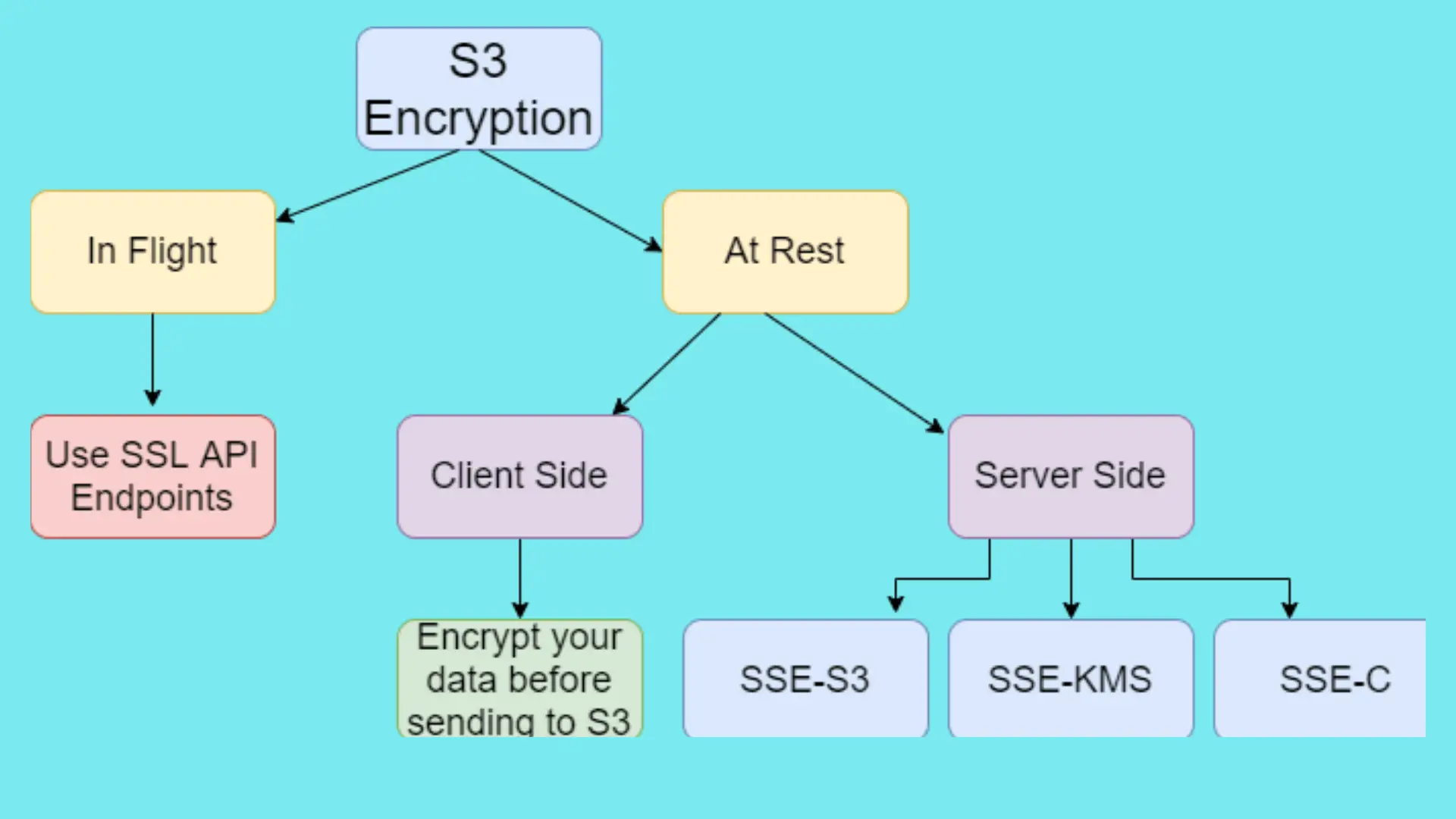
AWS S3 Encryption

Encryption In Flight:
By this time, you already know that you must encrypt your data while they are travelling. You can use Amazon S3 HTTPS/SSL API endpoints for the same.
Using HTTPS endpoints ensures that data that travels between you and Amazon S3 is always encrypted.
Basically, AWS S3 provides HTTP and HTTPS endpoints for you to work with an object. You might already know that HTTP is not encrypted while HTTPS connections are always encrypted.
To be precise, you are free to use the endpoint of your choice but for end-to-end security, it’s always recommended to use HTTPS to ensure data encryption in flight. Using HTTPS will ensure that, data transfer between your client and S3 is encrypted.
Encryption at Rest
- AWS S3 supports both Server Side Encryption and Client Side Encryption for your data at rest or stored data at the disk.
- In Server Side Encryption, when you upload an object, S3 encrypts it before storing on the disk and decrypts it before you access/download your data.
- In Client Side Encryption, you need to encrypt your data before sending it to AWS S3 and you are responsible for decrypting it after retrieving it from S3.
Don’t worry, we will know them in detail in upcoming sections.
Server Side Encryption
Server Side Encryption or SSE simply means that S3 as a server is responsible for the encryption and decryption of your objects. When you upload an object, Amazon S3 encrypts it before saving it to disk and decrypts it when you download/access it.
- Server-side encryption uses one of the strongest block ciphers available to encrypt your data, 256-bit Advanced Encryption Standard (AES-256).
- Server-side encryption encrypts only the object data, not object metadata.
Server Side Encryption Provides 3 Ways to Manage Keys

SSE-S3 : SSE using S3 Managed Key
- SSE-S3 is the server-side encryption with AWS S3 managed key.
- AWS S3 encrypts each object using a unique key handled and managed by AWS S3
- That unique key itself is encrypted using a separate master key for added security
- AWS responsible for rotating the master key regularly and a new master key is issued at least monthly
- The encrypted data, data keys, and master keys are all stored separately on secure devices
- You don’t pay anything extra for server-side encryption with S3 managed key or SSE-S3
SSE- KMS : SSE using AWS KMS Managed Key
- SSE-KMS is similar to S3 however here keys are stored and managed using KMS(Key Management Service) service
- You have better control over your keys in terms of who has permission to use the master key
- Having granular permission on your keys protects against unauthorized access to your objects in S3
- AWS KMS provides an audit log as well so you can know who tried to use your key to access an object and exactly when.
- Please note that you have to pay for using KMS service
SSE-C : SSE using Customer Provided Key
- SSE-C allows you to set your own encryption keys
- As the name says, AWS handles the encryption process but with the key you provide
- You provide the key as part of your request
- When using SSE-C, since you send a key as part of the request, only HTTPS is allowed, if you use HTTP, your request will be rejected
- You as a customer manage your own encryption key including the key rotation and you have full control of your key.
- Amazon S3 doesn’t store the encryption key you provide
- If you lose the encryption key, you lose the object
- You must have the mapping of which key was used with which object because
Client Side Encryption
- Client Side Encryption as the name says means that encryption and decryption occur on the client side
- The client is responsible for encrypting data before sending it to S3 and decrypting data after retrieving it from S3.
- You can use a client library such as the amazon S3 Encryption client.
- You as a client have two ways to manage keys
- Use an AWS KMS-managed customer master key
- Use a client-side master key
- You have end-to-end control on the entire encryption processing including the management of keys
Conclusion
I am sure you have a better idea of AWS S3 encryption now to protect your data in AWS S3. Let’s sum up some of the crucial points that we learnt.
- Always consider using AWS S3 HTTPS endpoint while working with your objects
- For simplicity and ease of use, you can use SSE-S3 or SSE-KMS
- Server Side Encryption encrypts only object data and not metadata.
- For end-to-end encryption use HTTPS for data transfer between your client and S3 and use server-side encryption or client-side encryption for data at rest as per your convenience.
I hope you found this post helpful.
Enjoyed the content?
Subscribe to our newsletter below to get awesome AWS learning materials delivered straight to your inbox.
If you are reading this, Please Please motivate me by-
- Adding a comment below on what you liked and what can be improved.
- Following Us On
- Share this post with your friends
Suggested Read:
- AWS S3 Storage Classes- All You Need to Know
- How to Create an S3 Bucket Policy using CloudFormation
- This is why S3 bucket names are unique globally
- Launch Your EC2 instance in an existing VPC using CloudFormation
- Attach an IAM to an EC2 Instance using CloudFormation
- Understand IAM PassRole to Secure your AWS Infrastructure
- How to Create S3 Bucket using CloudFomation
- AWS SQS Standard vs FIFO Queue
- How to Create S3 Bucket Policy using CloudFomation
- Provision ACM certificate using CloudFormation
- Create SSM Parameter using CloudFormation

3 thoughts on “AWS S3 Encryption: Way to Protect Your Data in S3”
Very useful blog. There is a typo in the “Encryption In Flight:” section. Change “betweek” to “between”
Thank you Ram, It’s updated now 🙂